Set Up Ansible with Kerberos on a PHX Development Desktop
Categories:
Overview
The Ansible development environment in the air-gapped PHX domain differs from the open-source PHX Development Environment (PXD). The PXD is fully open-source and part of the C2 Platform initiative. It uses Vagrant and Ansible without Kerberos, making it easier for quick setup and testing. In contrast, the PHX environment relies on Kerberos for authentication and vRA for infrastructure provisioning, without Vagrant. This setup is less suited for rapid Ansible development, as it lacks features like easy VM creation, snapshots, and automated environment management. For this reason, it’s often referred to as a pseudo development environment, involving more manual steps.
This guide explains how to simulate the PHX
Ansible development environment
setup. You’ll set up an Ubuntu 22.04 desktop VM named pxd-ubuntu-devtop using
Vagrant and Ansible. Once provisioned, connect to it via SSH or Remmina (for
RDP access). From there, perform Ansible tasks in this sandbox using Kerberos
authentication, mirroring the PHX domain setup.
This simulation facilitates understanding of how the Ansible development environment is set up and works in the PHX domain. It also forms a basis for creating and validating automation for managing the development environment. It enables developers to test and develop Ansible playbooks in a controlled, Kerberos-enabled environment without needing access to the actual air-gapped PHX domain. It emphasizes security best practices, such as using forwardable Kerberos tickets for seamless multi-hop authentication, while maintaining isolation for development and testing.
Prerequisites
Before starting, ensure you have the following:
- Setting Up the PHX Development Environment on Ubuntu 22.04: Set up your Ansible development desktop with Ansible, Vagrant, LXD, and VirtualBox on Ubuntu 22.04. Clone the PHX project directories to extend the base C2 development environment. Use this setup to configure essential base services, including the Microsoft AD domain controller and reverse proxy. Finally, access web-based services in the environment via a Firefox profile using the forward proxy for sandboxed access.
- Setting Up an Ansible Development Desktop: This guide details the steps to set up an Ansible Development Desktop using Ubuntu 22 that is similar to the desktop used within PHX domain.
Step 1: Connect to Ansible Development Desktop
Using Remmina, log in as tony with your password (e.g., Supersecret! for
testing).
Install required packages for Kerberos and Python development:
sudo apt install krb5-user libkrb5-dev python3-dev -y
Verify the Kerberos configuration tool version:
krb5-config --version
Show me
Check your current Kerberos tickets:
klist
Show me
Step 2: Customize Your Terminal
Create a file for Bash aliases to simplify your workflow and improve productivity:
nano ~/.bash_aliases
Add the following content (customize GIT_USER and GIT_MAIL as needed):
export ANSIBLE_INVENTORY=hosts-kerberos.ini
export EDITOR=nano
export GIT_USER='tclifton'
export GIT_MAIL='tony.clifton@dev.c2platform.org'
alias python='python3'
alias pip='pip3'
alias phx-env='source ~/.virtualenv/pxd/bin/activate'
alias phx-home='cd ~/git/gitlab/c2/ansible-phx'
alias phx='phx-home && phx-env'
alias phx-roles='phx && ansible-galaxy install -r roles/requirements.yml --force --no-deps -p roles/external'
alias phx-collections='phx && ansible-galaxy collection install -r collections/requirements.yml -p .'
alias phx-vault='ansible-vault edit secret_vars/development/main.yml'
# Function to securely set the Ansible Vault password using environment variable PX_ANSIBLE_VAULT_PASSWORD.
# The password will remain set for the duration of the shell session.
function phx-vault-password-env() {
local password
echo -n "Enter Ansible Vault passphrase: " >&2
read -s password
echo >&2 # Add a newline after the hidden input
export PX_ANSIBLE_VAULT_PASSWORD="$password"
echo "PX_ANSIBLE_VAULT_PASSWORD has been set for this shell session." >&2
export ANSIBLE_VAULT_PASSWORD_FILE=/usr/local/bin/vault-client.sh
}
# Function to securely set the Ansible Vault password using GNOME Keyring.
# The password will remain for the user session
function phx-vault-password() {
local pw=$(secret-tool lookup ansible vault 2>/dev/null)
if [ -z "${pw}" ]; then
echo "Password doesn't exist or is empty, lets add/set it!"
pw=$(secret-tool store --label 'Ansible Vault Password' ansible vault >&2)
echo "Vault password has been set." >&2
else
echo "Vault password is already set."
fi
export ANSIBLE_VAULT_PASSWORD_FILE=/usr/local/bin/vault-client-keyring.sh
}
export C2_HTTPS_SSH=https # Use HTTPS for SSH operations
history -s ansible -i hosts.ini -m win_ping pxd-ad
history -s ansible -i hosts.ini -m ping pxd-rproxy1
These aliases streamline common tasks, such as activating the virtual environment, navigating to project directories, and managing Ansible installations.
Step 3: Set Up Python Virtual Environment
Create a Python 3 virtual environment for Ansible to ensure isolation, stability, and reproducibility:
sudo apt update
sudo apt install virtualenv -y
mkdir ~/.virtualenv
DEB_PYTHON_INSTALL_LAYOUT='deb' virtualenv ~/.virtualenv/pxd -p python3
This setup prevents conflicts with system-wide Python packages and aligns with best practices for development environments.
Step 4: Clone Projects
Load your Bash configuration and install required tools:
source ~/.bashrc
sudo apt install git curl -y
curl -s -L https://gitlab.com/c2platform/phx/ansible/-/raw/master/clone.sh | bash
As a security best practice, always review the contents of scripts like
clone.sh before executing them via curl and bash. Download and inspect the
script first to ensure it aligns with your security standards.
Step 5: Install Ansible and Ansible Roles/Collections
Activate the environment and install dependencies:
source ~/.bashrc
phx
pip install -r requirements.txt
Use the predefined aliases to install Ansible collections and Ansible roles:
phx-collections
phx-roles
This step ensures all required Ansible components are installed in the virtual environment, promoting scalability and consistency.
Step 6: Set Ansible Vault Password
In order for user tony to use Ansible, he has to set the
Ansible Vault
password of the
inventory, which is
secret
. He utilizes
the phx-vault-password function:
phx
phx-vault-password
The output below shows the result of running the command:
(pxd) tony@pxd-ubuntu-devtop:~/git/gitlab/c2/ansible-phx$ phx
phx-vault-password
Password doesn't exist or is empty, lets add/set it!
Password:
Vault password has been set.
(pxd) tony@pxd-ubuntu-devtop:~/git/gitlab/c2/ansible-phx$
If you run the command for the first time, you are asked to set a password for the GNOME Keyring1. The Ansible Vault password will be stored there for convenience (you don’t have to provide the password each time you use Ansible) and also security. It is a safe place. The screenshot below shows the GNOME Keyring prompt asking for password and password confirmation.
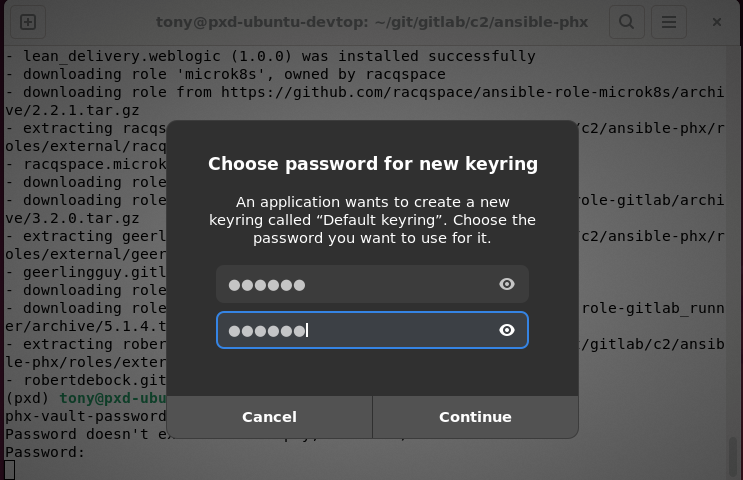
This securely handles sensitive data, following best practices for secret management in Ansible. For more details, see:
- Securely Accessing Ansible Vault in Development: Guideline for securely accessing Ansible Vault during development without storing passwords in plain files, using GNOME Keyring or environment variables.
Step 7: Ansible Ping
Verify the setup by pinging a Windows host:
ansible -m win_ping pxd-ad
Show me
Note:
We are implicitly using the inventory filehosts-kerberos.ini through the
environment variable ANSIBLE_INVENTORY. This is a modified version of
hosts.ini prepared for Kerberos authentication. Vagrant uses the hosts.ini
file, which relies on plain username and password authentication instead of
Kerberos. On pxd-ubuntu-devtop, we use Kerberos similarly to how it is used
within the PHX domain.Step 8: Ansible Provision
phx
ansible-playbook plays/mgmt/ad.yml
This step applies the Ansible playbook to provision resources, simulating PHX operations in your local environment.
Additional Information
- Securely Accessing Ansible Vault in Development
- Engineering with a "Pseudo" Development Environment
- Ansible Vault
- Setting Up the PHX Development Environment on Ubuntu 22.04
- Kerberos Authentication — Ansible Community Documentation
- Kerberos Ticket Properties - Kerberos V5 UNIX User's Guide
GNOME Keyring is a secure storage daemon for managing passwords, keys, and certificates in GNOME-based Linux environments. It provides encrypted storage and automatic unlocking during user sessions, enhancing security for sensitive data like Ansible Vault passwords. ↩︎
Feedback
Was this page helpful?
Glad to hear it! Please tell us how we can improve.
Sorry to hear that. Please tell us how we can improve.