Setup GitLab Container Registry
c2d-gitlab.Categories:
This how-to describes how create and use the
GitLab Container Registry
. This registry is not enabled by default in GitLab CE but it is enabled on default in this project by Ansible see group_vars/gitlab/registry.yml
Prerequisites
Overview
In this project we access the GitLab registry using URL https://registry.c2platform.org
via reverse proxy running on c2d-rproxy.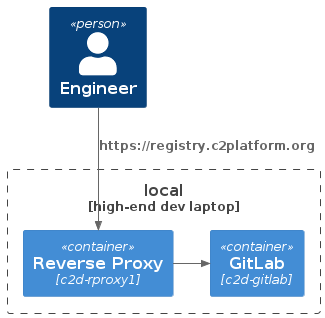
Start GitLab
Start GitLab instance created using Setup GitLab .
vagrant up c2d-gitlab
Verify
If create a GitLab project and navigate to Packages and registries you should see three options one of which is Container Registry.
Login and Push
To verify that the registry is working, you can try to push an image to it. In example below we use the node c2d-gitlab-runner for this purpose.
vagrant up c2d-gitlab-runner
Now we can test if we can login to the registry:
vagrant@c2d-gitlab-runner:~$ sudo su -
root@c2d-gitlab-runner:~# docker login registry.c2platform.org
Username: root
Password:
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded
root@c2d-gitlab-runner:~#
Download an image for example docker pull ubuntu tag it and then push it to a Gitlab project. For example if we created project c2platform/gitlab-docker-build
as part of
Setup GitLab
.
Pipeline
If you performs the steps in How-to Running GitLab CE pipelines in Kubernetes this also verifies the GitLab Container Registry is enabled and working correctly. TODO
Links
- Install GitLab Runner using the official GitLab repositories | GitLab
- robertdebock/ansible-role-gitlab_runner
Feedback
Was this page helpful?
Glad to hear it! Please tell us how we can improve.
Sorry to hear that. Please tell us how we can improve.